Mastering Software Engineering: Diagrams, Models, and Testing Techniques
Introduction to Hamming Code
INTRODUCTION
The collection of error-correction codes that may happen when moving data from the sender to the receiver is referred to as Hamming codes.
By identifying the state at which the problem happened, the hamming approach fixes the error.
HAMMING CODE’S PAST
R.W. Hamming developed the method known as the Hamming code to find faults.
Hamming code uses the connection between data and redundant bits and may be applied to data units of any length.
He worked on the issue of the error-correction technique and created the Hamming code, a family of progressively potent algorithms.
He released the Hamming Code in 1950, and it is still commonly used today in systems like ECC memory.
APPLICATIONS OF HAMMING CODE
- Satellites
- Computer Memory
- Modems
- PlasmaCAM
- Open connectors
- Shielding wire
- Embedded Processor
ADVANTAGES OF HAMMING CODE
- The hamming code approach is effective on networks where the data streams are provided for single-bit mistakes.
- In addition to helping you find bit errors, hamming code also enables you to indent the bit that contains the fault so that it may be fixed.
- Hamming codes are ideal for use in computer memory and single-error correction due to their simplicity of usage.
STEPS TO FIND THE HAMMING CODE
The additional parity bits are used by the hamming approach to enable the detection of single-bit errors.
- Step 1: Calculation of superfluous bit counts overall.
- Step 2: Determine where the duplicate bits are located.
- Step 3: Determine the values of these superfluous bits is the last step.
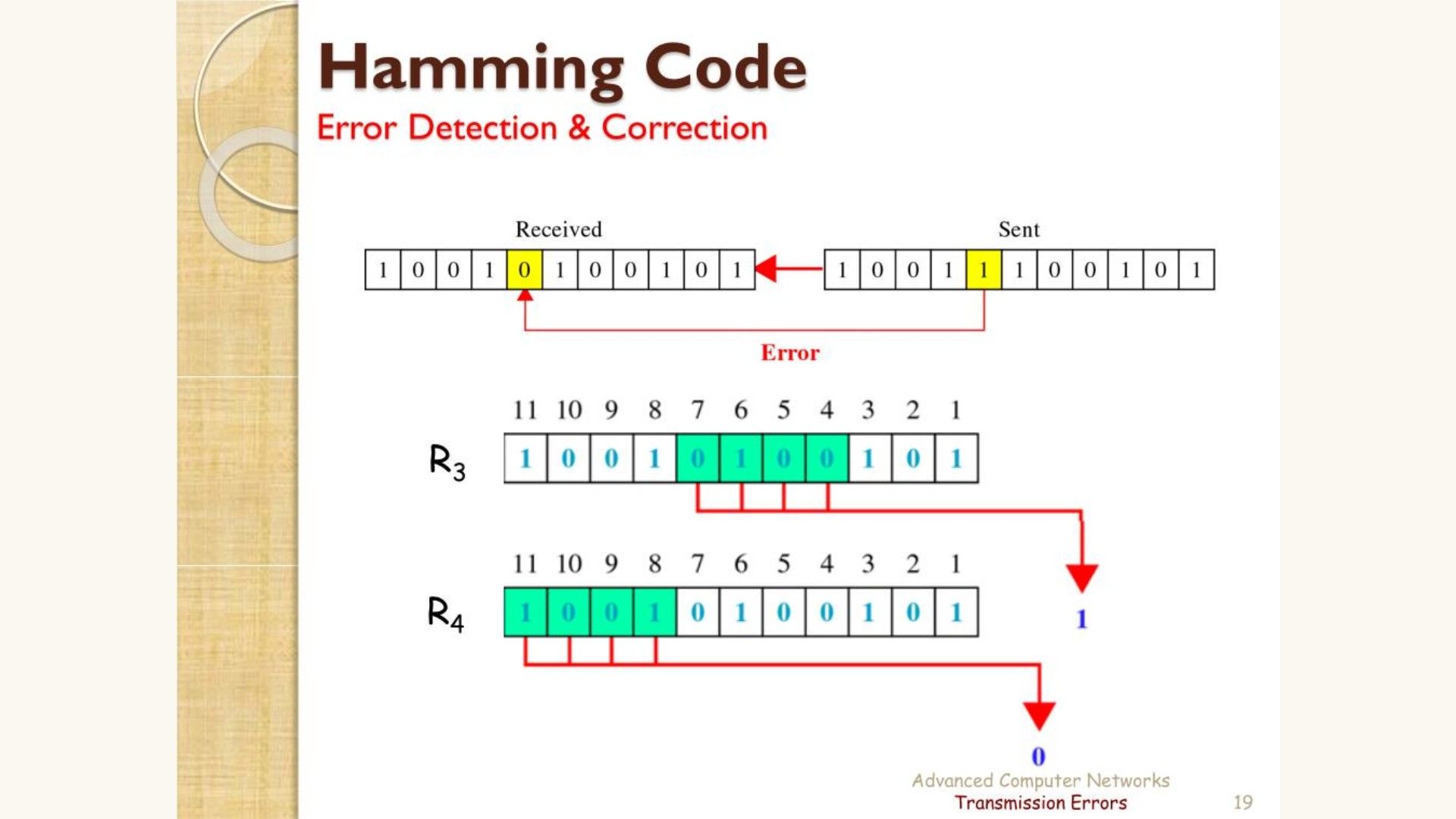
HAMMING CODE MESSAGE DECRYPTION
The receiver receives messages that must be recalculated in order to identify and repair problems.
The following stages are taken during the recalculation process:
- Determining how many unnecessary bits there are.
- Accurate placement of all the extra pieces.
- Verify parity
Conclusion
- Communication might result in the corruption of sent data.
- There are three types of bit errors:
1. Single Bit Errors
2. The Multiple Bit Error Burst Bit
- The term "single-bit error" refers to a change in a single bit over the whole data sequence.
- Multiple-bit errors occur when there is a change in two or more bits of a data sequence from transmitter to receiver.
- Burst errors occur when a group of bits in the data sequence change.
- A method of identifying mistakes in data conveyed from a transmitter to a receiver in a data communication system is called error detection.
- There are three categories of error codes.
1) Parity Verification
2) Longitudinal Redundancy Check (CRL)
3) Cyclic Redundancy Check (CRC) (LRC)
- A liner code called Hamming code is effective for detecting faults up to two instantaneous bit errors. Errors of a single bit are possible.
- R.W. Hamming developed the method known as the Hamming code to find faults.
- Hamming code is frequently used in satellites, computer memory, modems, embedded processors, etc.
- The hamming code technique's main advantage is that it works well on networks where data streams are provided for single-bit faults.
- The fact that the hamming code approach can only address single bits problems is its major flaw.
- With the aid of hamming code, we can carry out the operation of encrypting and decrypting the communication.
